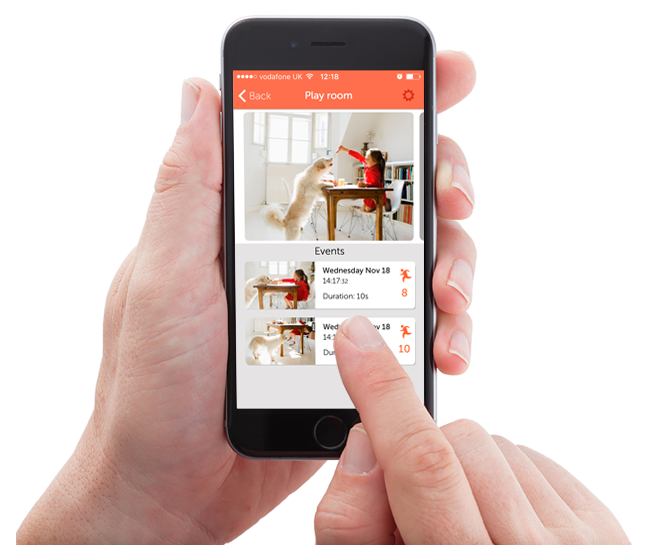
Tips on selecting home video security cameras
The latest home security cameras let you keep a watchful eye on your home, pets, children, cars and more during the day and at night. Our tips on what to look out for.
Tips on selecting home video security cameras Read More »